Is It Still Easy to Dox Someone From Skype
Being so used to live their lives on the internet, people usually don't consider the after-effects of sharing the most intimate and private details. Who thinks of the danger posting the good old granny's recipe of an apple pie, kids' photos from the graduation show, or geo marks of the vacation trip? Nobody does until the doxers step forward to invade your privacy.
What is doxing?
Doxing definition
The most common definition of doxing (or doxxing) is "a practice of searching and broadcasting of private authentic information about specific person or organization against their will, based on the internet technologies, evil-minded as a general rule". In some sources doxing is also identified as a powerful cyber-weapon with incredible aiming range which points its virtual guns at the far-out targets.
Origin of the term
There are two theories about the origin of this term:
- The word dox originates from "dropping dox", a hackers' society slang for gathering a dossier for the purpose of revenge. One of the first official mentions of the term was in 2003 when ransomware (doxware) blocking the personal data with an extortion following appeared.
- The etymology of the word doxing is just out of slangish documents/docs.
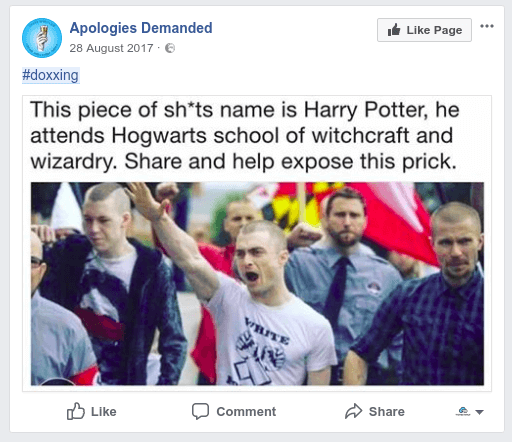
Who can become the victim?
Considering that the information is gathered not only out of public sources, aka social media accounts and comments & online chats. And it won't be only you (the person who blundered the information out), but also your friends and relatives, and other possible contacts, who will be perused and doxed out. Not to mention the fact that doxing tools can involve some hacking techniques with doxing through the IP or sniffing…
We come to the deplorable conclusion: in actual fact, ANYONE can become the doxing victim.
In 2017 the group of scientists from NYU and University of Illinois presented the report about doxing at the ACM Internet Measurement Conference, London. They found that most doxes include highly identifying information of the victims and their family members, such as their full legal names, phone numbers, real postal and IP addresses, online social networking accounts, and so on. The data they've introduced are embarrassing and shocking. Even though the average target type was the American male gamers in their 20s, it is absolutely clear, that everybody is involved.
| Read also: Top 7 Tips How to Protect Yourself from Phishing Scams
Is doxing illegal?
A difficult question to discuss, as all the law-connected points tend to be ambiguous. In case the information was found in some public open source and republished without significant harm, it is usually not considered to be cognizable by the court. When someone was doxed with the intention of further harassment, and the dox attack resulted into pain, suffering, and loss of amenity, or even in personal injury in some cases, it is considered as illegal activity.
Though, the US lawyer, publicist, and activist Susan Basco has a reasonable opinion of doxing being illegal in any case, whenever it is exercised against public employees or ordinary nationals. The United States has federal laws protecting public officers from deliberate doxing. At the same time, any dox attack on an ordinary person might be treated as harassment, cyberstalking, threats, etc., depending on the specific state legislation. There were attempts of misinformation actions, convincing doxing is legal. Well, people of sound mind and memory should reckon with the fact that an intent to threaten, harass, bully or extort anybody or actual fulfillment of all these cannot be legal, even when done by means of the internet.
The most vivid and tragic doxing attacks
Here are some examples of dox attacks which led to irreparable harm. Not to make the reader scared, but to show how real it is.
- A woman's naked photos (you do not expect to see them there, do you? it's just a link) were spread throughout the net. Thousands of men saw her, many of them started to mail her, and those letters were execrable. Posttraumatic stress disorder as a result.
- Another woman posted a couple of censorious comments on the popular Instagram account. The bullying was initiated by the admins, who uncovered her name, home address, telephone number, and even her parents' location. Moreover, they even gave the instructions of how exactly she should be harassed.
- The "lion killer case". In 2015 an illegal hunter was identified as a dentist from Minnesota. He became a real "pet peeve" for many people, who permanently offended him in social media. Besides, many protests took place near his office, and his home was vandalized.
- A 28 y.o. gamer was shot dead by the police as a result of a SWAT-attack that took place after doxing of the gamer's address by his rival.
If you need more examples, you can easily find them on the internet.
| Read also: General Data Protection Regulation Summary
How attackers get personal information about someone
Searching the information you post online yourself
The doxers gather the harvest right out of your own garden.
Being so unconcerned about their own security during internet interactions, people manage to leave so much personal information online, that it is enough for the doxer just to take a close look at public accessible data on Facebook, Google, Instagram, Twitter, Youtube, Skype, etc. to find out everything he/she wants to know about the victim, victim's friends and relatives.
Here are the most common methods used by doxers to dig out personal data:
Method 1: Targeting Name
The full name gives the doxer the access to many interesting things, but the most sensitive information is about your family. There is a vast variety of resources digging you up automatically such as PeekYou.com, ZabaSearch.com, PeopleFinders.com, and so forth. There are hundreds of similar resources actually. And the trolls use these websites to get close to your dirty laundry.
And even more, each site or forum where you register collects information given by you in the specific database, so-called WHOIS. A lot of personal information including name and phone number can be extracted out of this database even by the second-rate doxer.
Method 2: Targeting Email
It is another simple source that provides information about you without extra challenges. Are you sure that you're anonymous if your email doesn't contain your proper name? If you used this email during the registration on Facebook, you are not anonymous anymore. Knowing this email, the doxer can find your name on Facebook with the help of such link: https://www.facebook.com/search.php?q=email. Doxers just replace the word email in the link with the victim's email address and here it is – your account is shown. With all your photos, comments, personal information about your education and place of work, etc.
Almost the same way it works via Skype, where the search request can be fulfilled by the email.
Method 3: Targeting Area Code
This method is very common among doxers, as sometimes it's necessary to identify the right person from several people with identical names. For instance, a doxer needs to choose some John Smith out of a thousand of John Smiths. Let's imagine the particular one being doxed is from Florida. Trolls might go to http://www.allareacodes.com/area-code-lookup or any other area code lookup resource to narrow the search at least up to a hundred of J.Smiths.
Method 4: Targeting Phone Number
The same technique is used here as it was mentioned before in the "Targeting name" paragraph. It is sad to recognize that a lot of important authentic information we give to doxers on a silver platter ourselves.
Method 5: Targeting Website
So many people own websites for business or private purposes. And, of course, they fill in their data when registering these sites. Often without considering whether the "who.is protection" is available. If not, personal data can be hacked, that's that.
Method 6: Targeting Skype
Skype is being so unsafe due to its "seniority". And to the fact that we've registered there once to get in touch with people we are acquainted with and used our proper names as logins. Thus, we created the possibility to find out our real names and IPs with all the evident consequences.
| Read also: Social Engineering: What It Is and Why It Works
Using more advanced techniques
The current state of play assumes that there are more advanced technologies used by doxers in addition to those mentioned above. Though the traditional approach is still the easiest and the most conventional.
Wi-Fi sniffing
Free Wi-Fi at public places is the "bonne bouche" both for those who can't live a minute without posting and for the doxers who can easily get the fish caught it a real-time data flow. Goodbye, logins and passwords!
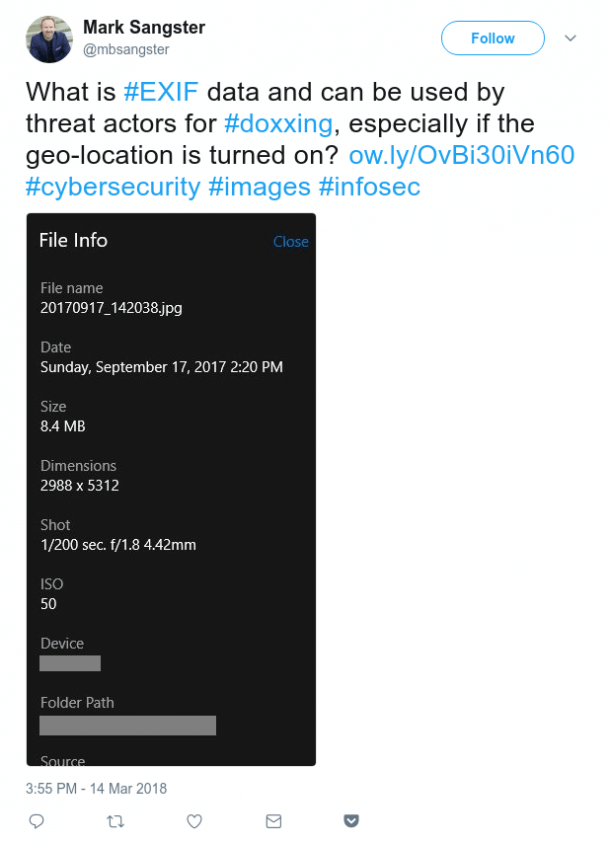
Analysing the metadata
Any document, media file, or photo was created sometime, somewhere, by someone. And all this information can be pulled out from the EXIF (Exchangeable Image File format) data. And if the person lives with the location switched on (or doesn't care whether it is), the EXIF data will strictly match the place where the photo was taken.
Doxing through IP logging
IP-logger is a special code, implemented into someone's device via email or any other type of the message, that will become a key to the IP-address of the victim with all the consequences that come with it.
How to protect yourself from doxing
1. Check what info about you can be found online and lock yourself down
Internet shelters a lot of the fleshpots, where doxers and trolls can dig up some dirt. So that is the launch point for you also. You should discover and estimate the "quantity and the quality" of data about you on the web. And then we go the same way back: they were tracing you this way, you can close all those doors opened to tighten your own privacy and security.
Method 1: Target Name
Remove your information from the data broker websites. Remove yourself from the sites' WHOIS database, mentioned before.
Never login the websites with questionable validity with "Login with Google" or "Login with Facebook" buttons. Doing this, you immediately share your name, phone number, in fact, all the data from your Google or Facebook account.
Method 3: Target Area Code
An effortless way of protection. Just do not identify it where possible.
Method 4: Target Phone Number
Repetitio est mater studiorum: remove your number out of all websites and databases where you can find it. To achieve the comprehensive picture on how much information about you is on the internet and how do doxers see it at their end make an anonymous search for yourself. We are sure the result will impress you.
Method 5: Target Websites
If the websites you own still don't have the who.is protection, have the trouble to buy and implement it. This will help to avoid a lot of troubles with domain protection either and shut the door in doxers' face.
Method 6: Target Skype
What security advice can we give here? Well, do not use your real name as a skype name, do not welcome strangers, do not adhere group chats. We'll avoid the rough formulation of "do not use skype". But we can confidently give the advice to use its numerous alternatives, which are more safe and proven.
| Read also: Which messaging apps are trustworthy?
2. Don't use your personal email to register on forums or other similar websites
The security level of the majority of forums leaves much to be desired. And there is no remedy here. Just create a special email account for the further registration on different forums. It will take you a couple of minutes but will certainly guard your original email against invasion.
3. Control your privacy settings on social networks
Care for your settings. It is not difficult to make your posts & photos visible only to your friends. Scan your friends list occasionally to extract those, who are not welcome anymore, as the changes in your real life can outrun your account condition.
4. Use two-factor authentication
Activate two-factor authentication in all your accounts, where this function of exists. It will not make a rescue but still, even discovering your password, the doxer will have to trouble his head with the following step to take.
5. Secure your passwords
Strong passwords are long (10 symbols +), unique, different in your various accounts, and if you change them regularly. So don't be lazy. In case your brain is exhausted to create passwords that follow all these requirements, some trusted password manager can help.
6. Protect your IP address with a VPN/Proxy
VPN can become an umbrella in the heavy rain for your internet traffic, even when you use the public place connection. Your personal data is being secured through encryption, moreover, it puts your IP-address out of sight. VPN with a strict no-logs policy is preferable. Some VPNs offers many useful extra-features, such as ads blocking or malware protection, which also reduce the risk of doxing.
7. Know your rights and use the law whenever possible
There is a program called "the right to be forgotten". The lucky inhabitants of European Union and Argentina can already take the advantage of it and delete all harmful information about themselves. Those who live in the USA have a lot more restrictions, though still there is a possibility to take the Google's option to remove all the content about yourself. There are some (a few, honestly) cases of successful DMCA takedown notices, though those who attained it had to pass through the "nine circles" of bureaucracy hell.
Conclusions
In this article we tried to answer the most common questions about doxing:
- What is doxing?
- How did the term "doxing" ("doxxing") appear?
- Who can become the victim?
- Is doxing legal?
We also showed how harmful doxing attacks can and provided the most vivid doxing examples with tragic ends.
Our goal was to give you a complete idea of how the attackers get information about the victims and how you can protect yourself from doxing.
And the conclusions of our investigation are simple: doxing is an illegal worldwide spread practice, and, by regret, with no tendency to decrease. Doxers' basic motivations are revenge, sick justice conceptions or competition. We all have at least one secret that will result in adverse consequences if being shared. Anybody can become a victim, without direct correlation with age, sex, race, occupation etc.
But if we start to care how we use the internet and what are we ready to share, following a couple of simple regulations, it will precisely lead to detection reduction. You can improve your cybersecurity by your own efforts.
Read more:
- Ransomware – to Pay or Not to Pay
- The Most Common Ways of Credit Card Fraud
- Email hacking protection
- 9 Data Protection Tips for Safe Online Shopping
- Malvertising: Can It Be Stopped?
- Data Protection in Universities under GDPR
Summary

Article Name
Doxing. What Is It? How to Dox? How to Protect Yourself from Doxing?
Description
The most common definition of doxing (or doxxing) is "a practice of searching and broadcasting of private authentic information about specific person or organization against their will, based on the internet technologies, evil-minded as a general rule".
Author
Anna
Publisher Name
Protectimus.com
Publisher Logo

You have Successfully Subscribed!
Source: https://www.protectimus.com/blog/doxing/
0 Response to "Is It Still Easy to Dox Someone From Skype"
Postar um comentário